Guest Author
Photo Credit: ordenador-ransomware via portal gda cc
According to TrendMicro, they saw a “172% increase in new ransomware families [in] 2016“. Even ransomware creators pitch it for sale as Ransomware-as-a-Service (RaaS). The threat of ransomware is real and ignoring it could lead to serious problems.
Numerous IT courses include content specific to security risks such as ransomware and cryptoware. The CompTIA Security+ course covers cryptography, attack types, malware, email security, business continuity, and all applicable topics regarding the threat from ransomware and how best to deter, mitigate and restore systems after an infection.
Training and education is always important as cyber threats evolve. Continued awareness and reinforcement of simple security measures will help to keep ransomware from interfering with your systems. This blog post explains how ransomware works and the correct steps to mitigate the risks ransomware presents.
What is Ransomware?
Ransomware actually sounds like what it does! Ransomware is a specific type of malware (malicious software) that generally locks up your system and demands a monetary ransom. Criminals use ransomware extensively in efforts to extort organizations and individuals. They often request payment with a crypto-currency, like Bitcoin, which is hard for authorities to track. One of the latest real-world examples is from the Krebs on Security report on the “San Francisco Rail System Hacker Hacked”, which details the San Francisco Rail System Being the target of Ransomware on 11 November 2016. (Also read about how the hacker was hacked!).
Don’t fall for ‘official looking’ Ransomware!
Ransomware may look official and include a warning that the FBI or other agency has detected illegal activity on your system (it typically claims that child pornography or illegal piracy were detected). These are all fake warnings. The FBI does not lock systems down with malware and demand ransom as restitution. A typical ransomware screen might look similar to the one below:
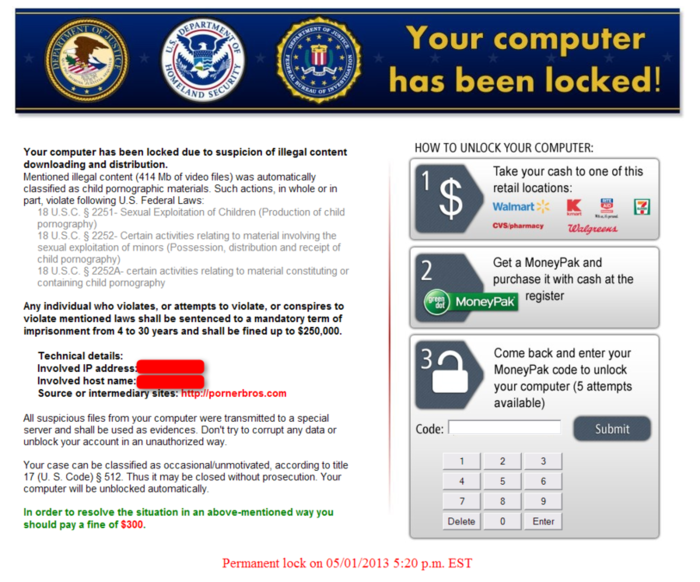
“Your Computer has been locked” with Cryptoware
More dangerous variants of Ransomware include a type that encrypt your system also. You may hear this referred to as cryptoware. Cryptolocker is a well known example of this type of ransomware. In this scenario, you may be locked out of your system(s), and many or all of the files will also be encrypted with a key that only the criminal has. In a typical scenario, the cryptoware demands a ransom, and then in most cases you will be provided a key in order to decrypt your system(s).
Organizations fall victim to ransomware and cryptoware often. Lately, hospitals are prime targets of ransomware attacks. One of the latest is the November 2016 infection of the UK’s National Health Services Northern Lincolnshire and Google Foundation Trust (NHS NGL). Few details were released about this attack, but we do know that Hollywood Presbyterian Hospital in California paid 40 Bitcoins to the criminals (which was about $17,000 at the time), according to an article in PC Magazine.
Should you or your organization pay the ransom?
Personally, I would not pay the ransom, but that is a difficult decision that each person or organization needs to make for themselves. I would say that if you do pay a ransom, you are essentially supporting the cyber criminals and that simply perpetuates the illegal activity. With some variants of Cryptoware, there have been occasions where after the ransom was paid, the criminals did not provide a decryption key (or the key did not work correct). Instead of paying the ransom, take proactive steps to counter the ransomware threat.
Practical Steps to Mitigate Ransomware
First, everyone needs to back up all their files and test the backup to ensure that when you need to restore the files, you know the process. Wherever the backups are stored, I highly recommend they be offline (or with an external encrypted cloud provider). If the backup file servers can get infected because they were on your network, you lose.
Secondly, everyone should perform all of the traditional cyber hygiene that perhaps was put on the back burner. While basic security and cyber hygiene is not sexy, it is vital. This is not new, but as a reminder this includes:
- Update and patch Operating Systems (hosts and servers) regularly
- Run and update end-point anti-virus, anti-malware software
- Restrict permissions (only use root or admin when absolutely required)
- Use email security and web browser protection
- Scan downloads for malware & PUPs (Potentially Unwanted Programs)
- Train staff to not use USB drives (USB drives are a frequent infection vector)
- Training staff frequently on social engineering threats and trends
Frequent Refresher Training for Staff is Critical
As many as 50% of users still click the link in phishing emails! Social engineering is an effective method for criminals to deliver Ransomware. US-CERT points out that an attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offer credentials to support their identity. As per US-CERT, users should be aware that phishing attacks may also appear to come from other types of organizations, such as charities. Attackers often take advantage of current events and certain times of the year, such as:
- Natural disasters (e.g., hurricane Katrina, Indonesian tsunami)
- Epidemics and health scares (e.g., H1N1)
- Economic concerns (e.g., IRS scams)
- Major political elections
- Holidays
Gateway Email Security
No matter how much training you give staff, email and attachments are still a risk. By using an email security gateway monitor, incoming and outgoing emails can be scanned for malware, phishing attacks, and spam.
Depending on the model, some have more sophisticated features as well, such as potentially blocking certain types of PII or PHI data. Examples of products includes McAfee Security for Email Services, Microsoft Exchange Online Protection (EOP), Proofpoint Enterprise Protection and Symantec Email Security Cloud. You should always perform your own research, testing and evaluation of any product before purchase.
Disable URLs and Hyperlinks in Outlook
If your institute uses Outlook, you may have some options to disable hyperlinks, or at least make them less easy to simply click on. This means that even if a phishing email sneaks through your email and spam filters, a person would have to copy and paste the URL into their browser.
The first and probably the easiest option is to configure Office ADMX Group Policy to turn on “Read As Plain Text to disable HTML viewing” which effectively means any URLs or hyperlinks in the email are not clickable. Many organizations prefer to use HTML formatting. However enabling plant text viewing by default means that a user cannot simply click a link (in a phishing email). This method gives a user time to think about their actions as they copy and paste the URL into their browser.
Additional Resources:
- Booz Allen Hamilton – Ransomware Reality Check – Getting Beyond The Headlines
- Malwarebytes Labs – How To Beat Ransomware: Prevent, Don’t React
- Sophos – Ransomware: Information And Prevention
- Sophos – The Current State of Ransomware
- Verizon – 2016 Data Base Investigative Report (DBIR)
- US-CERT – Cyber Security Tips
- US – CERT – Cryptolocker Ransomware Infections
- SearchSecurity- Comparing the Best Mail Security Gateways
- Tip 801 – Block Hyperlinks on Outlook
About the Guest Writer – John Stoner
Mr. Stoner has over 16 years of experience in the national security and defense sector working a variety of roles, including Cyber Threat Analyst, Cyber Counterintelligence Analyst and Cyber Instructor. He holds A+, Net+, CEH, CHFI, CEI, CISD and CISSP certifications. Connect with him on LinkedIn.
subscribe by email
Stay Ahead
Related Posts
-
Cyber Security
Cybersecurity Mindful Moments by Tara Lemieux
February 7, 2023
-
Uncategorized
How soft skills can improve employee retention
April 29, 2022
-
Business Communication
What is active listening and why do you need it in the workplace?
March 25, 2022
